Category: Ethereum
-
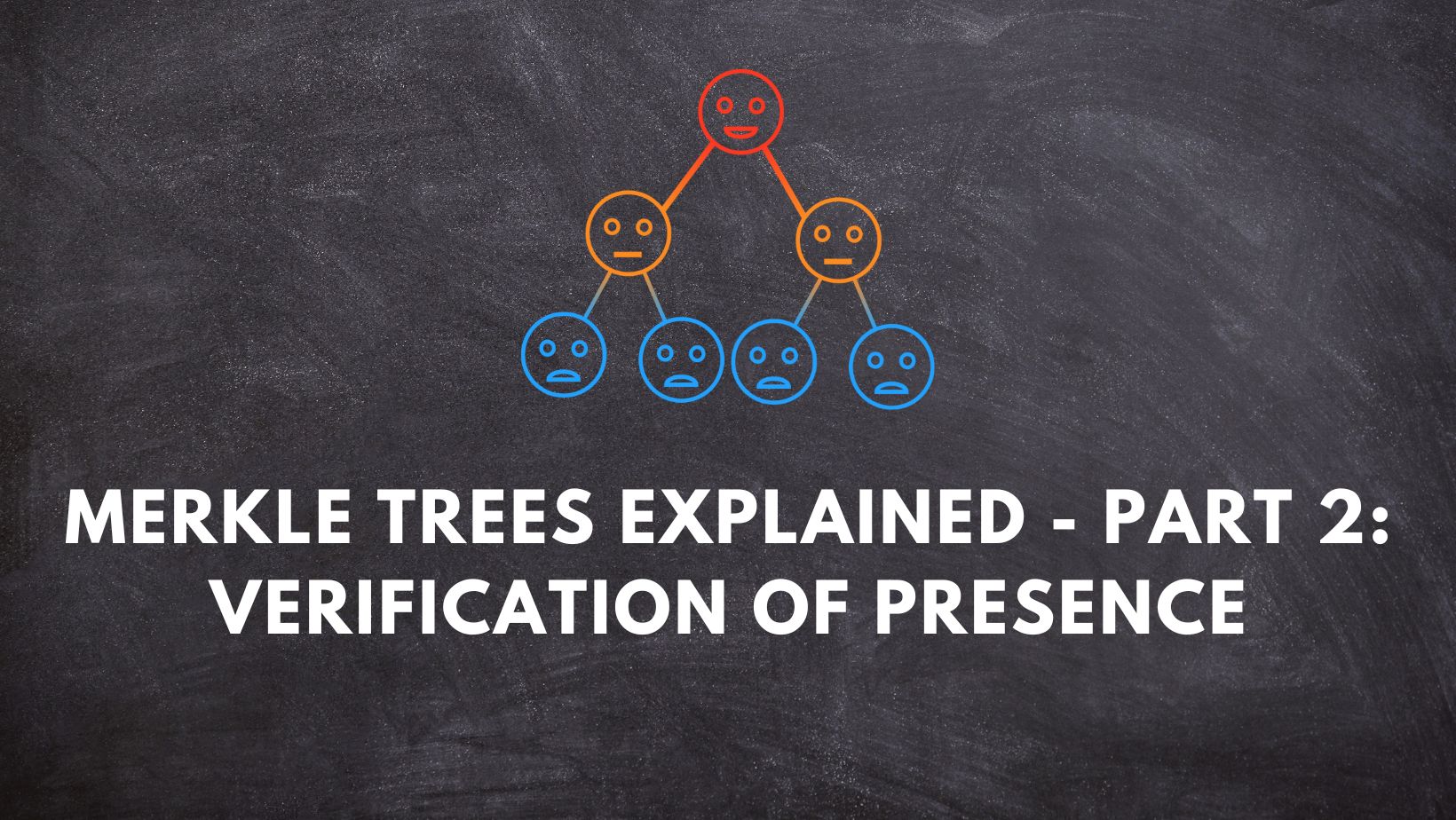
Merkle trees explained – Part 2: How verification of presence works
In part 1 of this article, we tried to understand what merkle trees are and the concept behind. We know that merkle trees help us in verifying whether a particular data point is the part of the tree ( merkle root ) or not. In this part, let’s go through exactly how this process of…
-

Merkle trees explained – Part 1: What are merkle trees?
If you are a dev / techie and if you have a high level understanding of blockchains, you surely have heard this buzzword: “Merkle trees”. Wikipedia says: In cryptography and computer science, a hash tree or Merkle tree is a tree in which every “leaf” (node) is labelled with the cryptographic hash of a data block,…
-

Solidity tips and tricks #2: Avoid storage data mutations and operations
EVM has three types of data storage locations: Storage Memory Calldata Each data location has a different purpose and using them appropriately will save us gas and money. Keep in mind that, in some situations, Solidity strictly enforces a default location. Storage When placed in storage, a variable is written on the blockchain. Everything that…
-

Basic overview of data types in solidity
Solidity is a high-level, object-oriented programming language that is used to write smart contracts and build D-apps. It also supports inheritance, libraries, and sophisticated user-defined types. Solidity is a statically typed language. That means, you will have to declare the type of variables in advance unlike javascript. Any programming language has basic data types and…
-

Understanding NFT Staking and how it works
Staking has been prominent in the crypto circles and has been a key component of various protocols. NFT staking follows a similar approach and should sound quite familiar to the folks who understand ERC20 staking / yield farming conceptually. Before we dive deep into NFT staking, do follow me on twitter for more such informative…
-

EIP-712 structured data hashing and signing explained
Ethereum for identity verification Cryptography is at the heart of blockchain technology. An identity in ethereum is represented by public-private keypair. Using this keypair and asymmetric cryptography, the origin of a transaction and its integrity are established. How? Let me try to explain it quickly. Let’s say that I have a public-private key pair. While…
